Your smart home is more vulnerable than you think. Every IoT device in your home (from your doorbell camera to your smart thermostat) creates potential entry points for cybercriminals. Understanding IoT port security isn't just for tech experts anymore; it's essential for anyone with connected devices. This guide will show you exactly how to audit your IoT devices, identify dangerous open ports, and secure your network before hackers exploit these vulnerabilities.
Understanding IoT Port Security: The Basics
IoT port security refers to the practice of monitoring, controlling, and securing the network ports that your smart devices use to communicate. Think of ports as numbered doorways on each device. Some need to stay open for functionality, but many are left unnecessarily exposed, creating serious security risks.
When manufacturers ship smart devices, they often prioritize convenience over security. This means devices arrive with default passwords, unnecessary services running, and ports left wide open. Cybercriminals exploit these weaknesses using automated scanners that continuously sweep the internet looking for vulnerable devices.
The consequences can be severe. Compromised IoT devices can be used to launch massive DDoS attacks, spy on your activities, steal personal data, or serve as stepping stones to access more valuable targets on your network like computers containing financial information.
Common IoT Ports and Their Risks
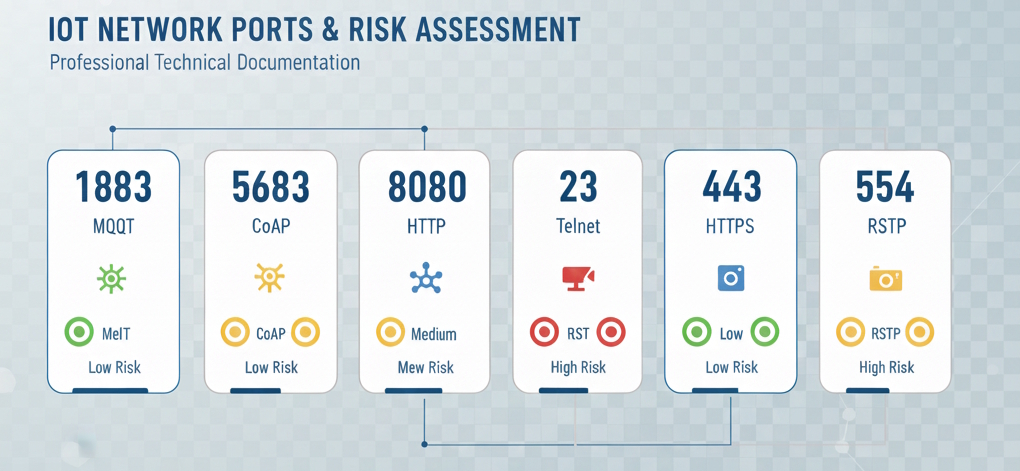
Different smart devices use specific ports for communication. Here are the most critical ones you need to monitor:
- Port 23 (Telnet): Legacy protocol still found in some IoT devices. Transmits all data including passwords in plaintext.
- Port 1883 (MQTT): Used by many smart home devices for lightweight messaging. Often unencrypted and vulnerable to interception.
- Port 8080 (HTTP Alternative): Common for web interfaces on cameras and smart hubs. Often uses weak or default credentials.
- Port 554 (RTSP): Real-Time Streaming Protocol for IP cameras. Often poorly secured, allowing unauthorized access to camera feeds.
Step-by-Step Guide: Auditing Your IoT Device Ports
Now let's get practical. Follow these steps to audit your smart home's security posture and identify vulnerable ports.
Step 1: Prepare Your Testing Environment
Create a spreadsheet listing every connected device in your home, including brand, model, MAC address, and assigned IP address. Choose your scanning tool: Nmap is the industry standard and free. For beginners, consider GUI options like Fing (available on mobile) or Angry IP Scanner. Run scans during low-usage periods to minimize potential disruption.
Step 2: Install and Configure Nmap
Nmap (Network Mapper) is a powerful, open-source tool for network discovery and security auditing.
Installation Instructions by Operating System
- Windows: Download the installer from nmap.org. Include Zenmap (the graphical interface) for easier use.
- macOS: Install via Homebrew with
brew install nmap, or download the disk image from nmap.org. - Linux: Install via your package manager. For Debian/Ubuntu:
sudo apt-get install nmap. For Red Hat/CentOS:sudo yum install nmap.
Step 3: Discover Devices on Your Network
First, identify all devices connected to your network and their IP addresses.
Basic network discovery command:
nmap -sn 192.168.1.0/24This performs a "ping scan" to discover live hosts without scanning their ports. Replace 192.168.1.0/24 with your actual network range. To find your network range, check your router's settings page (usually accessible at 192.168.1.1 or 192.168.0.1) or use ipconfig on Windows or ifconfig on macOS/Linux.
Cross-reference the output with your device inventory. Any unknown devices should be investigated immediately.
Step 4: Scan Individual Devices for Open Ports
Now scan each IoT device to see which ports are open and what services are running.
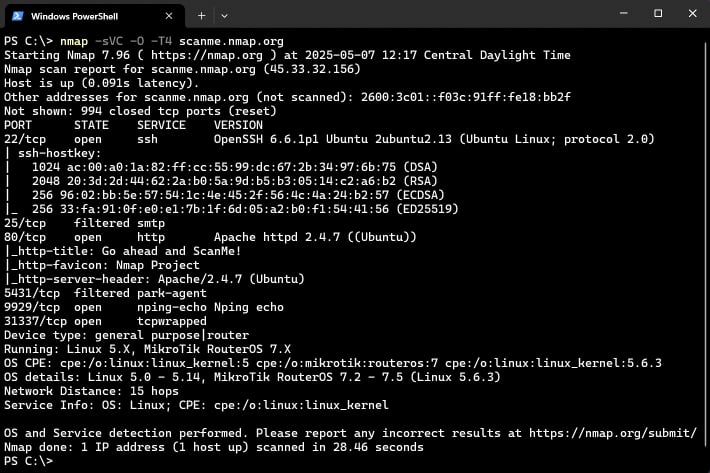
Comprehensive port scan command:
nmap -sV -p- 192.168.1.100Breaking down this command:
-sV: Probes open ports to determine service and version information.-p-: Scans all 65,535 ports (by default, Nmap only scans the 1,000 most common ports).192.168.1.100: Replace this with the IP address of your target device.
nmap -sV 192.168.1.100 for faster results. Only do comprehensive scans on devices that show concerning results in the initial scan.
Step 5: Analyze Your Results
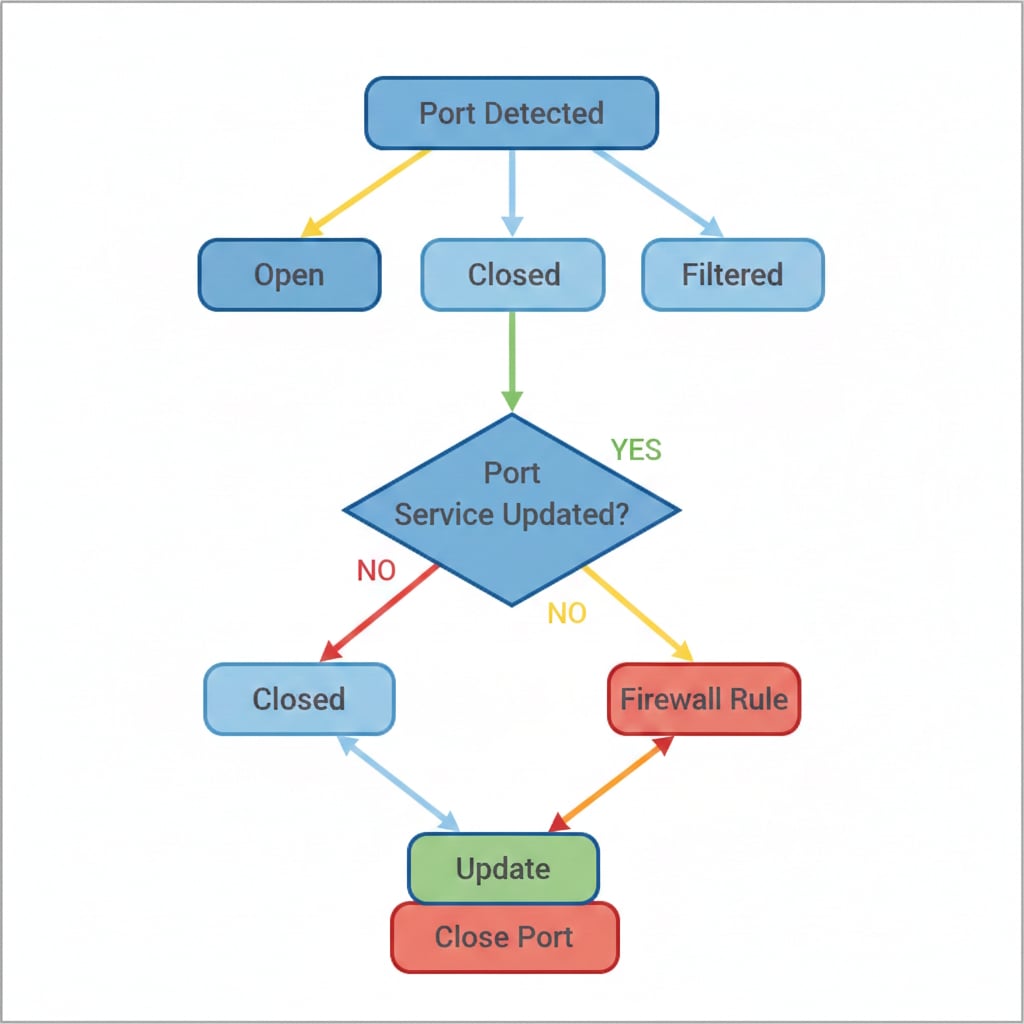
Understanding Nmap output is crucial for identifying vulnerabilities. The results show port status, services, and version numbers.
Port Status Meanings
- Open: The port is actively accepting connections. Not necessarily bad, but requires careful evaluation.
- Closed: The port is accessible but no service is listening.
- Filtered: A firewall or other security device is blocking access. This is ideal for ports you don't need to access externally.
Critical Red Flags That Demand Immediate Action
- Port 23 (Telnet) open on any device
- Port 21 (FTP) without TLS/SSL encryption
- Web interfaces on ports 80 or 8080 without HTTPS alternatives on port 443
- Port 22 (SSH) accessible with default or weak credentials
- UPnP (Universal Plug and Play) enabled and exposed to the internet
- Services showing version numbers with known CVE (Common Vulnerabilities and Exposures) entries
How to Research Service Vulnerabilities
When Nmap identifies a service version, search for "[service name] [version number] CVE" in your browser. For example, "OpenSSH 7.4 CVE" will show known security vulnerabilities. If critical vulnerabilities exist, prioritize updating or isolating that device.
Securing Your IoT Devices: Practical Steps
Discovering vulnerabilities is only half the battle. Now you need to fix them. Here's your action plan.
Immediate Actions for Every Device
- Change all default passwords: Use unique, strong passwords (minimum 16 characters with uppercase, lowercase, numbers, and symbols) for each device. Consider using a password manager like Bitwarden, 1Password, or KeePass.
- Update firmware immediately: Check manufacturer websites for the latest firmware versions. Enable automatic updates if available.
- Disable unnecessary features: If you don't use remote access, turn it off. Disable UPnP unless absolutely necessary.
- Enable encryption wherever possible: Use WPA3 on your Wi-Fi network (WPA2 if WPA3 isn't supported). Enable HTTPS/TLS for web interfaces.
Router-Level Protection
Your router is your first line of defense. Configuring it properly protects all connected devices simultaneously.
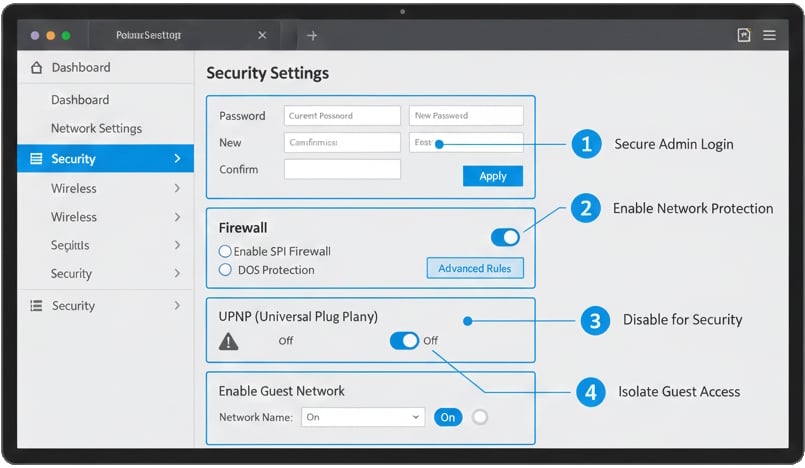
Essential Router Security Settings
- Change router admin credentials: Never use the default username and password printed on your router.
- Create a separate IoT network: Most modern routers support guest networks. Dedicate one exclusively to IoT devices to isolate them from computers and phones containing sensitive data.
- Disable WPS: Wi-Fi Protected Setup has known security vulnerabilities. Turn it off.
- Enable and configure firewall: Your router's built-in firewall should be active with default-deny rules for incoming connections.
- Disable remote management: Unless you have a specific need to manage your router from outside your home network, turn off this feature.
- Change default DNS servers: Consider using security-focused DNS services like Cloudflare (1.1.1.1) or Quad9 (9.9.9.9) which block access to known malicious domains.
Advanced Security Measures for Maximum Protection
Implement VLANs (Virtual Local Area Networks)
VLANs segment your network at a deeper level than guest networks. Enterprise routers and some prosumer models support VLANs, allowing you to create completely isolated network segments for IoT devices, computers, and guests. Even if an IoT device is compromised, attackers cannot reach your other network segments.
Deploy a Dedicated Network Firewall
Solutions like pfSense, OPNsense, or commercial options (Ubiquiti UniFi, Firewalla) provide advanced firewall capabilities, intrusion detection systems (IDS), and granular control over which devices can communicate with each other and the internet.
Continuous Network Monitoring
Tools like Wireshark or ntopng help you identify unusual traffic patterns that might indicate compromised devices. Look for unexpected outbound connections, high data usage from devices that should be idle, or communication with suspicious IP addresses.
Device-Specific Security Recommendations
Smart Cameras and Video Doorbells
- Disable cloud storage if you can use local storage (SD card, NAS)
- Enable two-factor authentication (2FA) on camera accounts without exception
- Position cameras to avoid capturing neighbors' property or public spaces
Smart Speakers and Voice Assistants
- Use the physical microphone mute button when having sensitive conversations
- Review and delete voice recordings regularly through the companion app
- Never link sensitive accounts (banking, email) to voice assistants
Smart Locks and Access Control
- Use time-limited access codes for guests rather than sharing master codes
- Review access logs weekly to detect unauthorized entry attempts
- Disable remote unlocking features if you don't need them
Maintaining Ongoing IoT Port Security
Security isn't a one-time task. Establish these ongoing practices to maintain protection over time.
Monthly Security Routine
Create a recurring calendar reminder to:
- Run a network discovery scan to verify all devices and check for unknown devices
- Check for firmware updates on all devices, prioritizing those with known vulnerabilities
- Review router logs for suspicious activity, failed login attempts, or unusual traffic patterns
- Run comprehensive port scans on a rotating subset of devices
Warning Signs of Compromised Devices
Watch for these indicators that might suggest devices have been compromised:
- Unexpected increases in network bandwidth usage
- Devices rebooting without explanation or behaving erratically
- Settings changing on their own (passwords reset, features enabled)
- New devices appearing on your network that you didn't add
- Unusual outbound connections to foreign IP addresses or suspicious domains
- Smart cameras with LED lights activating when you're not viewing them
Tools and Resources for Enhanced Security
Essential Security Tools
- Nmap: Industry-standard port scanner
- Fing: User-friendly network scanner with mobile apps
- Shodan: Search engine for internet-connected devices - search for your public IP to see what hackers see
- Wireshark: Network protocol analyzer for advanced traffic analysis
Recommended Online Resources
- OWASP IoT Project: Comprehensive IoT security best practices
- Mozilla Privacy Not Included: Privacy and security reviews of popular smart home products
- Consumer Reports Security Planner: Personalized security recommendations
- Most smart home devices have open ports that hackers actively scan. Regular audits using tools like Nmap help identify vulnerable ports before attackers exploit them.
- Change all default passwords immediately, update firmware regularly, and disable unnecessary features to dramatically reduce your attack surface.
- Isolate IoT devices on a separate network (VLAN or guest network) and implement firewall rules to prevent lateral movement if devices are compromised.
- Monitor your network monthly for suspicious activity, new unauthorized devices, and unexpected changes in device behavior or settings.
Conclusion
IoT port security isn't optional in 2025; it's essential for protecting your privacy, data, and network. With the average home containing 17 connected devices and hackers deploying increasingly sophisticated scanning tools, your smart home is only as secure as its weakest device.
Start with the basics this week: scan your network, change those default passwords, and isolate your IoT devices on a separate network. Then build on this foundation with regular monthly audits and continuous monitoring. Remember, cybersecurity is an ongoing journey, not a destination.
Your smart home should make your life easier and safer, not create new vulnerabilities. Take action today to ensure your connected devices remain under your control.
Frequently Asked Questions
Q: How often should I scan my IoT devices for open ports?
A: Perform basic network discovery scans monthly to check for new devices and verify existing ones. Run comprehensive port scans on all devices quarterly, or immediately after firmware updates, adding new devices, or noticing suspicious behavior.
Q: What's the biggest security mistake people make with IoT devices?
A: The most critical mistake is never changing default passwords. Attackers maintain extensive databases of default credentials for thousands of device models and automatically try them against every device they find. The second biggest mistake is enabling UPnP, which automatically opens ports without your knowledge, completely bypassing your router's firewall protections.
Q: What should I do if I discover a device with ports I can't close?
A: First, check for firmware updates as newer versions often close security holes. If updates don't help, use your router's firewall to block external access to those ports while still allowing local network access. For devices with unfixable critical vulnerabilities, seriously consider replacement with more secure alternatives. As a last resort, isolate the device on a separate VLAN with strict firewall rules.