Understanding how port checking works is essential for network administrators, developers, and IT professionals. Port checking is a fundamental network diagnostic technique that helps verify whether specific communication ports on a server or device are open, closed, or filtered. This technical guide explores the mechanisms behind port checking, revealing what happens when you test network connectivity and how these processes keep your systems running smoothly.
The Fundamentals of Network Ports and Communication
Before diving into the technical details of checking ports, it's important to understand what network ports actually are. Think of ports as numbered doorways on a computer or server. Each port corresponds to a specific service or application. For example, web servers typically use port 80 for HTTP traffic and port 443 for HTTPS connections.
When two computers communicate over a network, they use TCP/IP protocols to establish connections. The combination of an IP address and a port number creates a unique endpoint for data transmission. This addressing system allows multiple services to run simultaneously on a single device without interfering with each other.
TCP vs UDP Port Checking
Port checks typically focus on two main transport protocols: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). TCP connections require a three-way handshake, making them easier to verify. UDP is connectionless, which makes checking these ports more challenging and less reliable. Most port checking tools primarily test TCP ports because of their predictable connection behavior.
How Port Scanning Tools Actually Work
When you run a port check, several technical processes occur behind the scenes. The scanning tool sends specially crafted packets to the target IP address and port combination, then analyzes the response (or lack thereof) to determine the port's status.
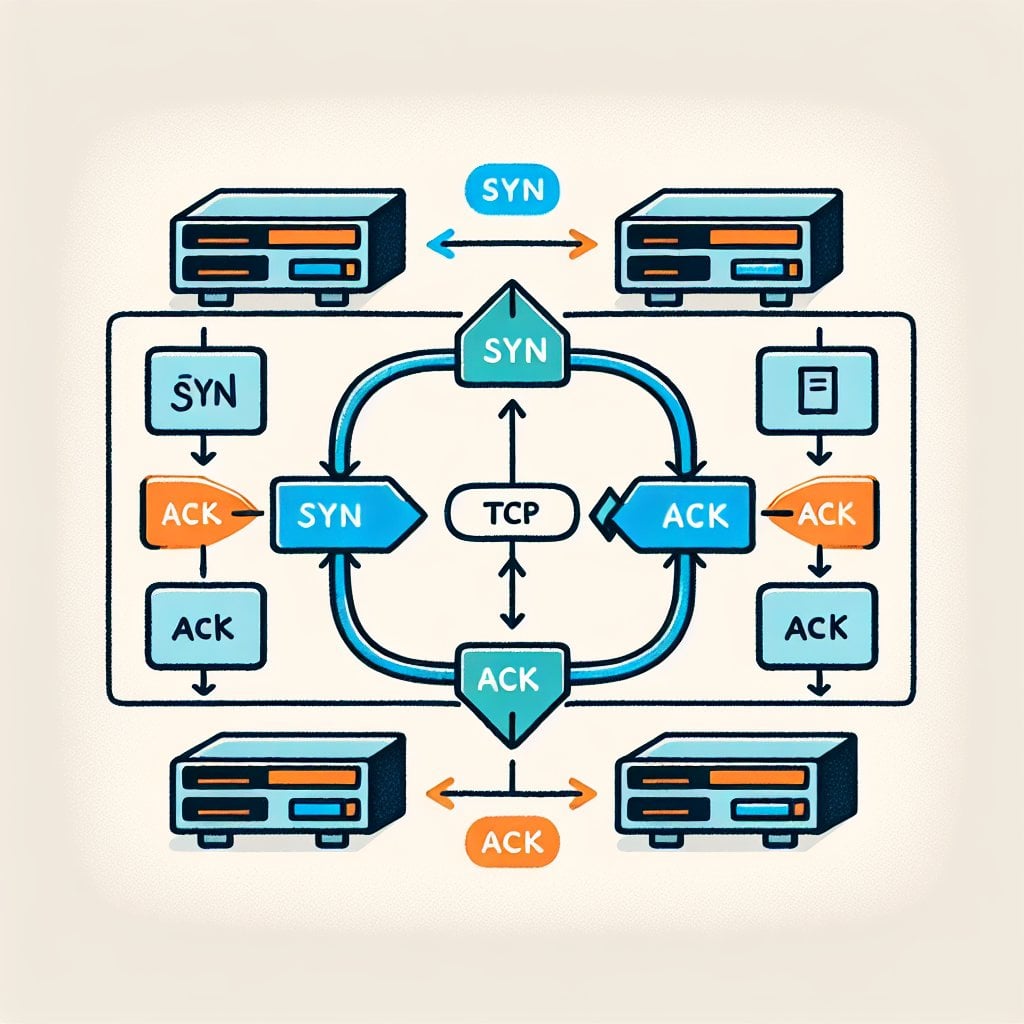
The TCP Three-Way Handshake Method
The most common technique for checking TCP ports is the SYN scan, also known as a half-open scan. Here's what happens step by step:
- Your scanning tool sends a SYN (synchronize) packet to the target port
- If the port is open, the target responds with a SYN-ACK (synchronize-acknowledge) packet
- The scanner then sends an RST (reset) packet instead of completing the handshake
- If the port is closed, the target responds with an RST packet immediately
- If there's no response, the port is likely filtered by a firewall
This method is efficient because it doesn't complete the full connection, making it faster and less detectable than establishing complete connections to each port.
Alternative Scanning Techniques
Beyond the standard SYN scan, several other techniques exist for checking ports. The TCP Connect scan completes the full three-way handshake, making it more reliable but also more visible in system logs. FIN scans send packets with the FIN flag set, which can sometimes bypass simple firewalls. NULL scans send packets with no flags set, exploiting how different operating systems respond to unusual traffic.
Each technique has specific use cases. Network administrators might use comprehensive scans during security audits, while developers typically need simple checks to verify that their applications are listening on the correct ports.
Interpreting Port Status Results
When you perform a port check, you'll receive one of several possible status results. Understanding what these mean helps you troubleshoot connectivity issues effectively.
Common Port States:
- Open: The port is actively accepting connections and a service is listening
- Closed: The port is accessible but no service is currently listening
- Filtered: A firewall or network device is blocking probe packets
- Open|Filtered: The tool cannot determine if the port is open or filtered
The distinction between these states matters significantly for troubleshooting. An open port indicates successful communication is possible. A closed port means you can reach the device, but nothing is listening on that specific port. Filtered results suggest network security measures are in place, which might require configuration changes to allow legitimate traffic.
Firewall and Security Implications
Modern firewalls can detect and respond to port scanning activities. Stateful firewalls track connection states and can identify scanning patterns. Some security systems implement rate limiting, which slows down or blocks repeated connection attempts from the same source. This is why aggressive scanning can sometimes trigger security alerts or temporary IP blocks.

Practical Applications and Tools
Port checking serves numerous practical purposes in network management and security. System administrators use it to verify that services are running correctly after configuration changes. Security teams conduct port scans to identify potential vulnerabilities before attackers can exploit them. Developers rely on these checks to ensure their applications are accessible on the intended ports.
Popular tools range from simple online checkers to sophisticated command-line utilities. Nmap remains the industry standard for comprehensive network scanning, offering dozens of scan types and detailed reporting. Telnet and netcat provide quick command-line options for testing individual ports. Cloud-based services offer convenient web interfaces for basic connectivity testing without installing software.
Key Takeaways:
- Port checking uses packet analysis to determine if network ports are open, closed, or filtered
- TCP scans rely on the three-way handshake mechanism, while UDP checks are less reliable
- Different scanning techniques serve different purposes, from stealth reconnaissance to thorough audits
- Understanding port states helps diagnose connectivity issues and improve network security
Conclusion
Port checking operates through sophisticated packet manipulation and response analysis. By sending carefully crafted network packets and interpreting the responses, these tools reveal critical information about network services and security configurations. Whether you're troubleshooting connectivity issues, hardening security, or verifying service availability, understanding these underlying mechanisms empowers you to use port checking tools more effectively. The technical processes may seem complex, but they follow logical patterns that become intuitive with practice and application.
FAQ
Port checking typically refers to testing one or a few specific ports to verify their status, while port scanning involves systematically checking multiple ports (sometimes thousands) on a target system. Port checking is usually done for legitimate troubleshooting or verification purposes, whereas port scanning is often associated with security auditing or reconnaissance activities.
Checking a single port usually takes only a few milliseconds to a few seconds, depending on network latency and whether the port responds quickly. Scanning multiple ports takes longer - checking all 65,535 possible ports could take several minutes to hours depending on the scanning speed, network conditions, and any rate limiting in place.
Yes, most modern firewalls and intrusion detection systems can detect port scanning activities, especially aggressive scans. Connection attempts are typically logged by the target system. However, stealthy scanning techniques like SYN scans are less likely to appear in application logs compared to full TCP connect scans. Security-conscious networks often implement alerts for suspicious scanning patterns.
Port status can change based on several factors: services may start or stop, firewalls might be reconfigured, network routes could change, or the system might be under varying load conditions. Additionally, some security systems implement dynamic responses that change behavior based on detected scanning activities or source IP reputation. Temporary network congestion or packet loss can also cause inconsistent results.
The legality depends on your jurisdiction and intent. Checking ports on systems you don't own or have explicit permission to test may violate computer fraud laws in many countries. Always obtain written authorization before scanning networks or systems you don't control. Even well-intentioned security research can be considered unauthorized access without proper permission. When in doubt, consult with legal counsel before conducting any scanning activities.